Authentication of your Powershell script
Firstly, we need to authenticate every request send to the Azure REST API. Authentication is based on Subscription and Tenant: the Tenant GUID can be found in the Azure Active Directory in the overview and the subscription can be found in most resources in the overview part.
You can then validate the context and create the authentication header for future calls inside the script.
Doing something useful
Now we have this initial part out of the way, we can do something useful with the rest of the script.
One thing we can do is list all of the non-secret values of the variables in the variable groups of the pipeline library. This is useful especially if there are a lot of variable groups in use, or if you are looking for where a specific value has been used. All of this can be cumbersome to find. To get the values for organization and project, simply move to the pipelines’ Library and look at the URL in the browser:
https://dev.azure.com/{organization}/{project}/_library?itemType=VariableGroups
First, we are going to retrieve all libraries within the project and put those in the $data variable.
Iterate to the data
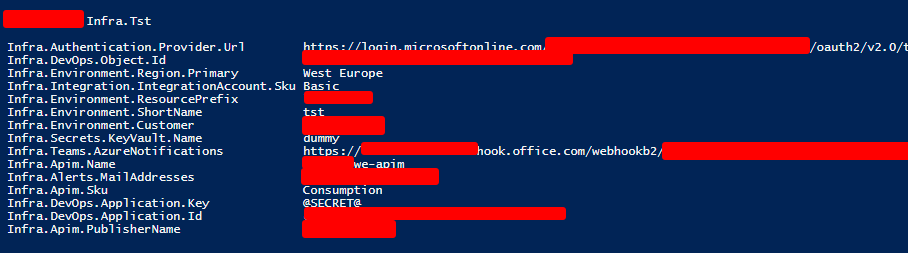
For each Variable group, we can loop through all the variables within to see the name and the values. We will then only see all of the variables with non-secret values. If the value is a secret, we should see “@SECRET@”, generated as a formatted output.
Output
This is only a small sample of the output. Depending on your setup this can grow to become a very long list.
In this blog post, we learned how to use PowerShell to query variable groups in Azure DevOps via the REST API. By authenticating our script, we ensured secure access to the API. We demonstrated how to retrieve and list non-secret values from variable groups, making it easier to manage and optimize our pipelines. Mastering PowerShell for Azure DevOps empowers us to enhance our development and deployment processes. Happy scripting!
Subscribe to our RSS feed